Yesterday was a very sad day for me...i sometimes like to play some games (Doom 3, Halflife 2, etc...) and linux just can't do it as good as windows...so i installed windows so i could play games...i still use linux as my primary OS but have windows just so i can play games from time to time...i was thinking what could bring linux to the next level so it could beat microsoft and become the primary OS for most of the computing nation...I decided linux needed the following improvements (comments on ones you think i missed):
Easier for home use; more media options --> direct X 10 and under support, hardware exelerated drivers, faster 3d, the option of simplicity, games working out-of-the-box; perfect hardware support and auto config; always up-to-date; pretty (xgl/compiz option that comes as default). Well that's all that i have time for today...cheers.
Tuesday, August 22, 2006
Friday, August 18, 2006
NetBeans 6.0 M2 - First look
Today NetBeans 6.0 M2 came out and i decided i would give it a try...i also downloaded the NetBeans Profiler 6.0 M2 and have it installed as well...i have included some screenshots and thaughts/sugestions:
The installer for Netbeans 6.0 M2 and NetBeans Profiler 6.0 M2 look basicly the same as the installers from NetBeans 5.5 beta 1/2. Once installed this is NetBeans 6.0 M2 booting up: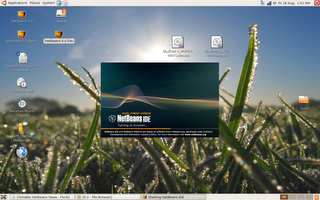
As soon as i had NetBeans 6.0 M2 running i opened the update center to update everything and add extra functionality...There are no changes to the update center that i can see...one feature i would really like to see in NetBeans is better "module management"...at the moment i can turn modules on and off but i would like to see a blacklist feature in the update center...so you can blacklist modules you never want to install (so for me that would include the modules that disable the default cvs support)...Here is a screen shot of the update center of NetBeans 6.0 M2: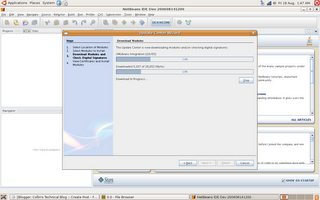
After i finished running the update center i had to restart the IDE...this is what it looked like:
Once the IDE is running again i looked around for some cool stuff...first i looked at full screen mode: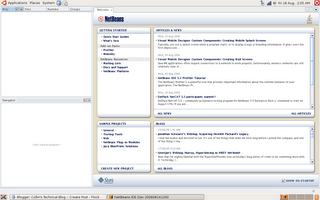
Pretty cool but i wish it support the whole screen like in the windows verion...maybe when jdk 6 Mustang comes out with gtk+ support then it will be able to get rid of the gnome panels...Also i can't wait to see how NetBeans will look under linux (gtk+) with Mustang...it will be awesome...because right now i can't say it is the pretties thing i have ever seen (although the interface is very intuitive and there is nothing netbeans could have really done about the way it looks....there are ways to buitify NetBeans (Substance) i would prefer native look and feel). Note: nothing against the UI team at NetBeans...the UI is great, very intuitive and user friendly and will be capped off on linux when Mustang comes out with gtk+ support to make it "sexy" on linux. Here is a screen shot of Full screen mode in Ubuntu 6.06 dapper: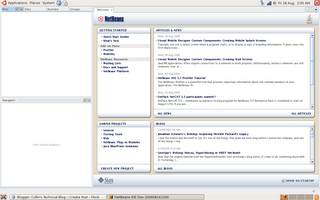 In a couple of days after using it for a little while i will report back with more things i like/dislike/like to see improved with screenshots.
In a couple of days after using it for a little while i will report back with more things i like/dislike/like to see improved with screenshots.
The installer for Netbeans 6.0 M2 and NetBeans Profiler 6.0 M2 look basicly the same as the installers from NetBeans 5.5 beta 1/2. Once installed this is NetBeans 6.0 M2 booting up:

As soon as i had NetBeans 6.0 M2 running i opened the update center to update everything and add extra functionality...There are no changes to the update center that i can see...one feature i would really like to see in NetBeans is better "module management"...at the moment i can turn modules on and off but i would like to see a blacklist feature in the update center...so you can blacklist modules you never want to install (so for me that would include the modules that disable the default cvs support)...Here is a screen shot of the update center of NetBeans 6.0 M2:

After i finished running the update center i had to restart the IDE...this is what it looked like:

Once the IDE is running again i looked around for some cool stuff...first i looked at full screen mode:

Pretty cool but i wish it support the whole screen like in the windows verion...maybe when jdk 6 Mustang comes out with gtk+ support then it will be able to get rid of the gnome panels...Also i can't wait to see how NetBeans will look under linux (gtk+) with Mustang...it will be awesome...because right now i can't say it is the pretties thing i have ever seen (although the interface is very intuitive and there is nothing netbeans could have really done about the way it looks....there are ways to buitify NetBeans (Substance) i would prefer native look and feel). Note: nothing against the UI team at NetBeans...the UI is great, very intuitive and user friendly and will be capped off on linux when Mustang comes out with gtk+ support to make it "sexy" on linux. Here is a screen shot of Full screen mode in Ubuntu 6.06 dapper:
 In a couple of days after using it for a little while i will report back with more things i like/dislike/like to see improved with screenshots.
In a couple of days after using it for a little while i will report back with more things i like/dislike/like to see improved with screenshots.
Monday, August 14, 2006
Things i want to see in future releases of Netbeans
I have been learning C/C++ and gtk+ and gtkmm (the C++ bindings to gtk+). So i was thinking what i would like to see from my favourite IDE, NetBeans and i thaught tha having a cross platform gui builder for C/C++ apps using gtk+/gtkmm would be cool...gtk+ and gtkmm are cross platform so all NetBeans would have to do is create a killer gui builder like Matisse...I am very excited to try out the new Matisse in NetBeans 5.5 and NetBeans 6.0. I also recently dound out from Roumen Strobl that Jdk Mustang supports gtk++...this make me very happy because i am a linux user (i have not had windows on my laptop for about 3 months :) and i am very happy with ubuntu :)). Anyway sorry if my thaughts are a little scrambled but it is late over here in Canada. Cheers.
This is what i have set as my nickname for MSN/Yahoo/ICQ/etc.. enjoy :)
Have you had enough with windows? Yeah you have...becuase there is somthing much better...it's called linux ;) Get it today...it is free!!
This is what i have set as my nickname for MSN/Yahoo/ICQ/etc.. enjoy :)
Have you had enough with windows? Yeah you have...becuase there is somthing much better...it's called linux ;) Get it today...it is free!!
Saturday, August 12, 2006
Endless Information
I am setting some goals for myself for this year and in the future...Here is a list of all the things i would like to acomplish this school year (September to June).
1. Work hard at school and stay on the honor role all year
2. Do the best i can do (give a full effort)
Programming objectives (over the next couple of years)
1. Make sure i know all of J2SE like the back of my hand and make sure i know all the new Mustang API's
2. Learn J2ME and all of its API's
3. Learn J2EE and all the fun stuff that comes along with it.
4. Learn C
5. Learn C++
6. Learn the linux C API's (gtk)
7. Learn the linux C++ API's (gtkmm)
8. Learn C# and Mono
9. Learn some scripting languages like js, perl, groovy, beanshell, etc...
10. Learn Python
11. Keep up to date on all of the langauges and thier API's
It is quite the list but i think it is possable to do...it is a lot of learning but it will be fun :)
1. Work hard at school and stay on the honor role all year
2. Do the best i can do (give a full effort)
Programming objectives (over the next couple of years)
1. Make sure i know all of J2SE like the back of my hand and make sure i know all the new Mustang API's
2. Learn J2ME and all of its API's
3. Learn J2EE and all the fun stuff that comes along with it.
4. Learn C
5. Learn C++
6. Learn the linux C API's (gtk)
7. Learn the linux C++ API's (gtkmm)
8. Learn C# and Mono
9. Learn some scripting languages like js, perl, groovy, beanshell, etc...
10. Learn Python
11. Keep up to date on all of the langauges and thier API's
It is quite the list but i think it is possable to do...it is a lot of learning but it will be fun :)
Wednesday, August 09, 2006
Ignorance Kills
I was googling around looking for something interesting and come across an article called "Is You Son a Computer Hacker?" by Reginald Gibbons. I thaught i would look interesting so i went and started reading... after a couple minuites i was very, very upset because the article was total BS!! After a little bit of thinking i thaught it might be a joke but i found that it was not...i was frustrated by his ignorance in writting about something he had apsolutly no clue about. I will give you an overview of the article with my thaughts on each part.
How to determine if your kid is a Hacker Acording to Reginald Gibbons
1. Has your son asked you to change ISPs?
Gibbons: "If your child is becoming a hacker, one of his first steps will be to request a change to a more hacker friendly provider."
Me: This is tottal BS...changing to a different ISP is not a sign of becoming a hacker...especialy if you are switching from slow AOL...
2. Are you finding programs on your computer that you don't remember installing?
Gibbons: "Your son will probably try to install some hacker software." ... "Popular hacker software includes 'Comet Cursor', 'Bonzi Buddy' and 'Flash'."
Me: [[Comet Cursor: A program which allows websites to change your mouse cursor when you are on their website to get the full effect of the webpage]]. It is by no means a hacker program AT ALL. You would have to be a complete idiot to think so!! [[Bonzi Buddy: A web enhancing program packaged with various other programs]]...this is just a little app that is packed with spyware/malware/adware that helps you browse the internet...hackers have apsolutly no uses for this program...what are they going to do with it? ask the monkey what to do next? At the end of Gibbons list is 'Flash'...when i say this is was just shocked that somebody could be soo ignorant...Flash has no uses for hackers at all!! All it does is enhance the experiance of internet users.
3. Has your child asked for new hardware?
Gibbons: "Computer hackers are often limited by conventional computer hardware. They may request 'faster' video cards, and larger hard drives, or even more memory. " ... "If your son has requested a new 'processor' from a company called 'AMD', this is genuine cause for alarm. AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips. They use child labor extensively in their third world sweatshops, and they deliberately disable the security features that American processor makers, such as Intel, use to prevent hacking. AMD chips are never sold in stores, and you will most likely be told that you have to order them from internet sites. Do not buy this chip! This is one request that you must refuse your son, if you are to have any hope of raising him well."
Me: First off as a geek i love getting new hardware...not because i am a hacker and am "limited by conventional harware" but because i enjoy getting the best performance from my machine. Gibbons mentions that hackers may request hardware like a faster videocard, a larger harddrive or more memory...A hacker would not prosper by having a faster videocard..it would not effect him at all...most hacking is done through a console unlike most hacker movie show (eg. Swordfish and the hacking GUI). Then he comes to saying that "AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips." This is the one of the stupidest thing i think i have ever heard... [[AMD is the second largest microprocessor producer in the world]] and just because they leave thier processors more open so they can be overclocked easier does not mean they are more hacker friendly. [[Most computers you buy retail now have AMD chips in them, because they are less expensive, and much quicker, thus enhancing the computing experience]].
4. Does your child read hacking manuals?
Gibbons: "There are, unfortunately, many hacking manuals available in bookshops today. A few titles to be on the lookout for are: 'Snow Crash' and 'Cryptonomicon' by Neal Stephenson; 'Neuromancer' by William Gibson; 'Programming with Perl' by Timothy O'Reilly; 'Geeks' by Jon Katz; 'The Hacker Crackdown' by Bruce Sterling; 'Microserfs' by Douglas Coupland; 'Hackers' by Steven Levy; and 'The Cathedral and the Bazaar' by Eric S. Raymond." ... "If you find any of these hacking manuals in your child's possession, confiscate them immediately."
Me: Sure there are many hacker books on the market...it is an interesting topic. [[Oh man...Programming With Perl? Your son would not like to become a hacker, but rather a coder for a large computer software company or internet company. Thanks, dad, for crushing his dreams of one day becoming a multimillionaire.]]
5. How much time does your child spend using the computer each day?
Gibbons: "If your son spends more than thirty minutes each day on the computer, he may be using it to DOS other peoples sites." ... "This can take up to eight hours."
Me: Most teens don't spend thier time on the computer using Dos to gain control of other peoples computer...they spend their time playing games and don't harm anything. By the way Dos'ing is more commonly known as 'flooding'. [[DOS'ing usually doesn't take 8 hours, although I can see that on AOL...It'd take 8 hours just to send out that many signals to one system, and more than likely it wouldn't be effective. ]]
6. Does your son use Quake?
Gibbons: "Quake is an online virtual reality used by hackers. t is a popular meeting place and training ground, where they discuss hacking and train in the use of various firearms. Many hackers develop anti-social tendencies due to the use of this virtual world, and it may cause erratic behaviour at home and at school."
Me: Quake is a GAME not a virtual reality used by hackers to train. Train in the use of variouse firearms? It is just a game...a first person shooter...the guns are not real!!
7. Is your son becoming argumentative and surly in his social behaviour?
Gibbons: "As a child enters the electronic world of hacking, he may become disaffected with the real world. He may lose the ability to control his actions, or judge the rightness or wrongness of a course of behaviour. This will manifest itself soonest in the way he treats others. Those whom he disagrees with will be met with scorn, bitterness, and even foul language. He may utter threats of violence of a real or electronic nature."
Me: Just because a child is interested in computers doesn't mean he will become disconnected with the "real world". Hackers are people too, and they function like all other people...just becuase they are hackers doesn't mean they fit the hacker stereo type... Also note that adolence could be effecting thier behavior.
8. Is your son obsessed with "Lunix"?
Gibbons: "BSD, Lunix, Debian and Mandrake are all versions of an illegal hacker operation system, invented by a Soviet computer hacker named Linyos Torovoltos, before the Russians lost the Cold War. It is based on a program called 'xenix', which was written by Microsoft for the US government. These programs are used by hackers to break into other people's computer systems to steal credit card numbers. They may also be used to break into people's stereos to steal their music, using the "mp3" program. Torovoltos is a notorious hacker, responsible for writing many hacker programs, such as "telnet", which is used by hackers to connect to machines on the internet without using a telephone.
Your son may try to install 'lunix' on your hard drive. If he is careful, you may not notice its presence, however, lunix is a capricious beast, and if handled incorrectly, your son may damage your computer, and even break it completely by deleting Windows, at which point you will have to have your computer repaired by a professional."
Me: When i read this section i was enraged...Lunix is a usinx based operating system for the commador 64...if your kid is still using one of those you should consider upgrading. First off linux is not an illegal operating system!! Lunix is different from every other example Gibbons gave... the rest use the linux kernel where Lunix has it's own. The linux kernel developed by Linyos Torovoltos is not based on xenix but is inspired by Minix. I have no clue where Gibbons comes up with his facts but i have yet to find one that is true. I have no clue what gibbons was doing when he wrote this article but this section is TOTTAL BS and makes no sence what so ever. [[Break into their stereos? In case you didn't notice when you were setting up your system, you didn't hook your stereo up to your computer...or wait, did you? God knows what happened when you set that thing up. MP3 files are compressed CD Audio files, and are used widely in the daily range of activities. And what's this bullsh*t about not noticing if Linux is installed? IT'S A TOTALLY DIFFERENT OPERATING SYSTEM THAT REPLACES WINDOWS!!! It's impossible not to notice it. It'd be clear as day when your dumb ass couldn't figure out why the f*ck your system had completely changed. And Linux is very easily removed by inserting your Compaq Recovery CD. And just for your info, when you send your computer back to the manufacturer, they're going to just restore it using the recovery CD, and laugh all day because of how idiotic you are.]]
9. Has your son radically changed his appearance?
Gibbons: "If your son has undergone a sudden change in his style of dress, you may have a hacker on your hands. Hackers tend to dress in bright, day-glo colors. They may wear baggy pants, bright colored shirts and spiky hair dyed in bright colors to match their clothes. They may take to carrying "glow-sticks" and some wear pacifiers around their necks. (I have no idea why they do this) There are many such hackers in schools today, and your son may have started to associate with them. If you notice that your son's group of friends includes people dressed like this, it is time to think about a severe curfew, to protect him from dangerous influences."

Me: In the section above Gibbons mentions that the creator of the linux kernel, Linyos Torovoltos is a computer hacker...to the left is a picture of him. Does he meet the description of a hacker acording to Gibbons? No because hes is NOT a hacker. [[I believer you're referring to the ever-growing group of stylists known as "ravers". They go to parties known as raves, and usually are on some form of sedative or the like. Special-K, i.e. Ketamine is highly popular, because it is easy to find and cheap to purchase. It is cat tranquilizer in small doses, and horse tranquilizer in large doses. Nextly, E, or extasy, is the next most popular drug. It is ingested in the form of a pill, and cause people to "roll" at raves, because of the intense lightshows. If your son was wearing raver clothing, more than likely you shouldn't worry about him being a hacker, but rather being under the influence of some drug or another. Nice detective work, Sherlock.]]
10. Is your son struggling academically?
Gibbons: "
If your son is failing courses in school, or performing poorly on sports teams, he may be involved in a hacking group, such as the infamous "Otaku" hacker association. Excessive time spent on the computer, communicating with his fellow hackers may cause temporary damage to the eyes and brain, from the electromagnetic radiation. This will cause his marks to slip dramatically, particularly in difficult subjects such as Math, and Chemistry. In extreme cases, over-exposure to computer radiation can cause schizophrenia, meningitis and other psychological diseases. Also, the reduction in exercise may cause him to lose muscle mass, and even to start gaining weight. For the sake of your child's mental and physical health, you must put a stop to his hacking, and limit his computer time drastically.
I encourage all parents to read through this guide carefully. Your child's future may depend upon it. Hacking is an illegal and dangerous activity, that may land your child in prison, and tear your family apart. It cannot be taken too seriously."
Me: Computers help chiI was googling around looking for something interesting and come across an article called "Is You Son a Computer Hacker?" by Reginald Gibbons. I thaught i would look interesting so i went and started reading... after a couple minuites i was very, very upset because the article was total BS!! After a little bit of thinking i thaught it might be a joke but i found that it was not...i was frustrated by his ignorance in writting about something he had apsolutly no clue about. I will give you an overview of the article with my thaughts on each part.
How to determine if your kid is a Hacker Acording to Reginald Gibbons
1. Has your son asked you to change ISPs?
Gibbons: "If your child is becoming a hacker, one of his first steps will be to request a change to a more hacker friendly provider."
Me: This is tottal BS...changing to a different ISP is not a sign of becoming a hacker...especialy if you are switching from slow AOL...
2. Are you finding programs on your computer that you don't remember installing?
Gibbons: "Your son will probably try to install some hacker software." ... "Popular hacker software includes 'Comet Cursor', 'Bonzi Buddy' and 'Flash'."
Me: . It is by no means a hacker program AT ALL. You would have to be a complete idiot to think so!! ...this is just a little app that is packed with spyware/malware/adware that helps you browse the internet...hackers have apsolutly no uses for this program...what are they going to do with it? ask the monkey what to do next? At the end of Gibbons list is 'Flash'...when i say this is was just shocked that somebody could be soo ignorant...Flash has no uses for hackers at all!! All it does is enhance the experiance of internet users.
3. Has your child asked for new hardware?
Gibbons: "Computer hackers are often limited by conventional computer hardware. They may request 'faster' video cards, and larger hard drives, or even more memory. " ... "If your son has requested a new 'processor' from a company called 'AMD', this is genuine cause for alarm. AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips. They use child labor extensively in their third world sweatshops, and they deliberately disable the security features that American processor makers, such as Intel, use to prevent hacking. AMD chips are never sold in stores, and you will most likely be told that you have to order them from internet sites. Do not buy this chip! This is one request that you must refuse your son, if you are to have any hope of raising him well."
Me: First off as a geek i love getting new hardware...not because i am a hacker and am "limited by conventional harware" but because i enjoy getting the best performance from my machine. Gibbons mentions that hackers may request hardware like a faster videocard, a larger harddrive or more memory...A hacker would not prosper by having a faster videocard..it would not effect him at all...most hacking is done through a console unlike most hacker movie show (eg. Swordfish and the hacking GUI). Then he comes to saying that "AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips." This is the one of the stupidest thing i think i have ever heard... and just because they leave thier processors more open so they can be overclocked esiar does not mean they are more hacker friendly.
4. Does your child read hacking manuals?
Gibbons: "There are, unfortunately, many hacking manuals available in bookshops today. A few titles to be on the lookout for are: 'Snow Crash' and 'Cryptonomicon' by Neal Stephenson; 'Neuromancer' by William Gibson; 'Programming with Perl' by Timothy O'Reilly; 'Geeks' by Jon Katz; 'The Hacker Crackdown' by Bruce Sterling; 'Microserfs' by Douglas Coupland; 'Hackers' by Steven Levy; and 'The Cathedral and the Bazaar' by Eric S. Raymond." ... "If you find any of these hacking manuals in your child's possession, confiscate them immediately."
Me: Sure there are many hacker books on the market...it is an interesting topic.
5. How much time does your child spend using the computer each day?
Gibbons: "If your son spends more than thirty minutes each day on the computer, he may be using it to DOS other peoples sites." ... "This can take up to eight hours."
Me: Most teens don't spend thier time on the computer using Dos to gain control of other peoples computer...they spend their time playing games and don't harm anything. By the way Dos'ing is more commonly known as 'flooding'.
6. Does your son use Quake?
Gibbons: "Quake is an online virtual reality used by hackers. t is a popular meeting place and training ground, where they discuss hacking and train in the use of various firearms. Many hackers develop anti-social tendencies due to the use of this virtual world, and it may cause erratic behaviour at home and at school."
Me: Quake is a GAME not a virtual reality used by hackers to train. Train in the use of variouse firearms? It is just a game...a first person shooter...the guns are not real!!
7. Is your son becoming argumentative and surly in his social behaviour?
Gibbons: "As a child enters the electronic world of hacking, he may become disaffected with the real world. He may lose the ability to control his actions, or judge the rightness or wrongness of a course of behaviour. This will manifest itself soonest in the way he treats others. Those whom he disagrees with will be met with scorn, bitterness, and even foul language. He may utter threats of violence of a real or electronic nature."
Me: Just because a child is interested in computers doesn't mean he will become disconnected with the "real world". Hackers are people too, and they function like all other people...just becuase they are hackers doesn't mean they fit the hacker stereo type... Also note that adolence could be effecting thier behavior.
8. Is your son obsessed with "Lunix"?
Gibbons: "BSD, Lunix, Debian and Mandrake are all versions of an illegal hacker operation system, invented by a Soviet computer hacker named Linyos Torovoltos, before the Russians lost the Cold War. It is based on a program called 'xenix', which was written by Microsoft for the US government. These programs are used by hackers to break into other people's computer systems to steal credit card numbers. They may also be used to break into people's stereos to steal their music, using the "mp3" program. Torovoltos is a notorious hacker, responsible for writing many hacker programs, such as "telnet", which is used by hackers to connect to machines on the internet without using a telephone.
Your son may try to install 'lunix' on your hard drive. If he is careful, you may not notice its presence, however, lunix is a capricious beast, and if handled incorrectly, your son may damage your computer, and even break it completely by deleting Windows, at which point you will have to have your computer repaired by a professional."
Me: When i read this section i was enraged...Lunix is a usinx based operating system for the commador 64...if your kid is still using one of those you should consider upgrading. First off linux is not an illegal operating system!! Lunix is different from every other example Gibbons gave... the rest use the linux kernel where Lunix has it's own. The linux kernel developed by Linyos Torovoltos is not based on xenix but is inspired by Minix. I have no clue where Gibbons comes up with his facts but i have yet to find one that is true. I have no clue what gibbons was doing when he wrote this article but this section is TOTTAL BS and makes no sence what so ever.
9. Has your son radically changed his appearance?
Gibbons: "If your son has undergone a sudden change in his style of dress, you may have a hacker on your hands. Hackers tend to dress in bright, day-glo colors. They may wear baggy pants, bright colored shirts and spiky hair dyed in bright colors to match their clothes. They may take to carrying "glow-sticks" and some wear pacifiers around their necks. (I have no idea why they do this) There are many such hackers in schools today, and your son may have started to associate with them. If you notice that your son's group of friends includes people dressed like this, it is time to think about a severe curfew, to protect him from dangerous influences."
Me: In the section above Gibbons mentions that the creator of the linux kernel, Linyos Torovoltos is a computer hacker...to the left is a picture of him. Does he meet the description of a hacker acording to Gibbons? No because hes is NOT a hacker.
10. Is your son struggling academically?
Gibbons: "
If your son is failing courses in school, or performing poorly on sports teams, he may be involved in a hacking group, such as the infamous "Otaku" hacker association. Excessive time spent on the computer, communicating with his fellow hackers may cause temporary damage to the eyes and brain, from the electromagnetic radiation. This will cause his marks to slip dramatically, particularly in difficult subjects such as Math, and Chemistry. In extreme cases, over-exposure to computer radiation can cause schizophrenia, meningitis and other psychological diseases. Also, the reduction in exercise may cause him to lose muscle mass, and even to start gaining weight. For the sake of your child's mental and physical health, you must put a stop to his hacking, and limit his computer time drastically.
I encourage all parents to read through this guide carefully. Your child's future may depend upon it. Hacking is an illegal and dangerous activity, that may land your child in prison, and tear your family apart. It cannot be taken too seriously."
Me: Computers help childern learn...i am done commenting on Gibbons total disregard to the truth and the facts. [[Well since you bought a new computer, emissions standards have virtually eliminated all radiation by computers, disproving your brain and eye damage theory. Most hackers are very intelligent, and excel in such subjects as math and foreign languages. And for everyone's knowledge, meningitis is NOT A PSYCHOLOGICAL DISEASE!!! IT'S BACTERIAL!!!]]
Note: text enclosed by [[]] is quoted from here
Conclusion:
Answering Gibbons questions:
1. Yes...i have changed my ISP a couple times [i wanted a faster conection].
2. I have flash on my linux laptop (the other programs do not work on linux i believe)
3. Yes i have asked for new hardware for variose computers in my house.
4. Yes i read hacking manuals because they are interesting (The unofficial guide to ethical hacking)
5. I spend many many hours a day on my computer. A lot more than 30 minuites a day...if i had the restriction i would die.
6. I have never played Quake but i have played quake 4 and 3...
7. No...just because i am a geek doesn't mean i do not have a life
8. Yes i love linux :)
9. Sometimes for fun :)
10. I only struggle accademicly when i don't work
So...acording to Gibbons i am a hacker. (Note that Gibbons is using the term 'Hacker' in a foul way. As in breaking the law.) I am not denying that i am a hacker...i will leave it up to you to decide (see this [note the bottom text])
Note: the term hacker takes on many meanings. Some of which are:
1. One who is proficient at using or programming a computer; a computer buff.
2. One who uses programming skills to gain illegal access to a computer network or file
ldern learn...i am done commenting on Gibbons total disregard to the truth and the facts.
Note: text enclosed by [[]] is quoted from here
Conclusion:
Answering Gibbons questions:
1. Yes...i have changed my ISP a couple times [i wanted a faster conection].
2. I have flash on my linux laptop (the other programs do not work on linux i believe)
3. Yes i have asked for new hardware for variose computers in my house.
4. Yes i read hacking manuals because they are interesting (The unofficial guide to ethical hacking)
5. I spend many many hours a day on my computer. A lot more than 30 minuites a day...if i had the restriction i would die.
6. I have never played Quake but i have played quake 4 and 3...
7. No...just because i am a geek doesn't mean i do not have a life
8. Yes i love linux :)
9. Sometimes for fun :)
10. I only struggle accademicly when i don't work
So...acording to Gibbons i am a hacker. (Note that Gibbons is using the term 'Hacker' in a foul way. As in breaking the law.) I am not denying that i am a hacker...i will leave it up to you to decide (see this [note the bottom text])
Note: the term hacker takes on many meanings. Some of which are:
1. One who is proficient at using or programming a computer; a computer buff.
2. One who uses programming skills to gain illegal access to a computer network or file
How to determine if your kid is a Hacker Acording to Reginald Gibbons
1. Has your son asked you to change ISPs?
Gibbons: "If your child is becoming a hacker, one of his first steps will be to request a change to a more hacker friendly provider."
Me: This is tottal BS...changing to a different ISP is not a sign of becoming a hacker...especialy if you are switching from slow AOL...
2. Are you finding programs on your computer that you don't remember installing?
Gibbons: "Your son will probably try to install some hacker software." ... "Popular hacker software includes 'Comet Cursor', 'Bonzi Buddy' and 'Flash'."
Me: [[Comet Cursor: A program which allows websites to change your mouse cursor when you are on their website to get the full effect of the webpage]]. It is by no means a hacker program AT ALL. You would have to be a complete idiot to think so!! [[Bonzi Buddy: A web enhancing program packaged with various other programs]]...this is just a little app that is packed with spyware/malware/adware that helps you browse the internet...hackers have apsolutly no uses for this program...what are they going to do with it? ask the monkey what to do next? At the end of Gibbons list is 'Flash'...when i say this is was just shocked that somebody could be soo ignorant...Flash has no uses for hackers at all!! All it does is enhance the experiance of internet users.
3. Has your child asked for new hardware?
Gibbons: "Computer hackers are often limited by conventional computer hardware. They may request 'faster' video cards, and larger hard drives, or even more memory. " ... "If your son has requested a new 'processor' from a company called 'AMD', this is genuine cause for alarm. AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips. They use child labor extensively in their third world sweatshops, and they deliberately disable the security features that American processor makers, such as Intel, use to prevent hacking. AMD chips are never sold in stores, and you will most likely be told that you have to order them from internet sites. Do not buy this chip! This is one request that you must refuse your son, if you are to have any hope of raising him well."
Me: First off as a geek i love getting new hardware...not because i am a hacker and am "limited by conventional harware" but because i enjoy getting the best performance from my machine. Gibbons mentions that hackers may request hardware like a faster videocard, a larger harddrive or more memory...A hacker would not prosper by having a faster videocard..it would not effect him at all...most hacking is done through a console unlike most hacker movie show (eg. Swordfish and the hacking GUI). Then he comes to saying that "AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips." This is the one of the stupidest thing i think i have ever heard... [[AMD is the second largest microprocessor producer in the world]] and just because they leave thier processors more open so they can be overclocked easier does not mean they are more hacker friendly. [[Most computers you buy retail now have AMD chips in them, because they are less expensive, and much quicker, thus enhancing the computing experience]].
4. Does your child read hacking manuals?
Gibbons: "There are, unfortunately, many hacking manuals available in bookshops today. A few titles to be on the lookout for are: 'Snow Crash' and 'Cryptonomicon' by Neal Stephenson; 'Neuromancer' by William Gibson; 'Programming with Perl' by Timothy O'Reilly; 'Geeks' by Jon Katz; 'The Hacker Crackdown' by Bruce Sterling; 'Microserfs' by Douglas Coupland; 'Hackers' by Steven Levy; and 'The Cathedral and the Bazaar' by Eric S. Raymond." ... "If you find any of these hacking manuals in your child's possession, confiscate them immediately."
Me: Sure there are many hacker books on the market...it is an interesting topic. [[Oh man...Programming With Perl? Your son would not like to become a hacker, but rather a coder for a large computer software company or internet company. Thanks, dad, for crushing his dreams of one day becoming a multimillionaire.]]
5. How much time does your child spend using the computer each day?
Gibbons: "If your son spends more than thirty minutes each day on the computer, he may be using it to DOS other peoples sites." ... "This can take up to eight hours."
Me: Most teens don't spend thier time on the computer using Dos to gain control of other peoples computer...they spend their time playing games and don't harm anything. By the way Dos'ing is more commonly known as 'flooding'. [[DOS'ing usually doesn't take 8 hours, although I can see that on AOL...It'd take 8 hours just to send out that many signals to one system, and more than likely it wouldn't be effective. ]]
6. Does your son use Quake?
Gibbons: "Quake is an online virtual reality used by hackers. t is a popular meeting place and training ground, where they discuss hacking and train in the use of various firearms. Many hackers develop anti-social tendencies due to the use of this virtual world, and it may cause erratic behaviour at home and at school."
Me: Quake is a GAME not a virtual reality used by hackers to train. Train in the use of variouse firearms? It is just a game...a first person shooter...the guns are not real!!
7. Is your son becoming argumentative and surly in his social behaviour?
Gibbons: "As a child enters the electronic world of hacking, he may become disaffected with the real world. He may lose the ability to control his actions, or judge the rightness or wrongness of a course of behaviour. This will manifest itself soonest in the way he treats others. Those whom he disagrees with will be met with scorn, bitterness, and even foul language. He may utter threats of violence of a real or electronic nature."
Me: Just because a child is interested in computers doesn't mean he will become disconnected with the "real world". Hackers are people too, and they function like all other people...just becuase they are hackers doesn't mean they fit the hacker stereo type... Also note that adolence could be effecting thier behavior.
8. Is your son obsessed with "Lunix"?
Gibbons: "BSD, Lunix, Debian and Mandrake are all versions of an illegal hacker operation system, invented by a Soviet computer hacker named Linyos Torovoltos, before the Russians lost the Cold War. It is based on a program called 'xenix', which was written by Microsoft for the US government. These programs are used by hackers to break into other people's computer systems to steal credit card numbers. They may also be used to break into people's stereos to steal their music, using the "mp3" program. Torovoltos is a notorious hacker, responsible for writing many hacker programs, such as "telnet", which is used by hackers to connect to machines on the internet without using a telephone.
Your son may try to install 'lunix' on your hard drive. If he is careful, you may not notice its presence, however, lunix is a capricious beast, and if handled incorrectly, your son may damage your computer, and even break it completely by deleting Windows, at which point you will have to have your computer repaired by a professional."
Me: When i read this section i was enraged...Lunix is a usinx based operating system for the commador 64...if your kid is still using one of those you should consider upgrading. First off linux is not an illegal operating system!! Lunix is different from every other example Gibbons gave... the rest use the linux kernel where Lunix has it's own. The linux kernel developed by Linyos Torovoltos is not based on xenix but is inspired by Minix. I have no clue where Gibbons comes up with his facts but i have yet to find one that is true. I have no clue what gibbons was doing when he wrote this article but this section is TOTTAL BS and makes no sence what so ever. [[Break into their stereos? In case you didn't notice when you were setting up your system, you didn't hook your stereo up to your computer...or wait, did you? God knows what happened when you set that thing up. MP3 files are compressed CD Audio files, and are used widely in the daily range of activities. And what's this bullsh*t about not noticing if Linux is installed? IT'S A TOTALLY DIFFERENT OPERATING SYSTEM THAT REPLACES WINDOWS!!! It's impossible not to notice it. It'd be clear as day when your dumb ass couldn't figure out why the f*ck your system had completely changed. And Linux is very easily removed by inserting your Compaq Recovery CD. And just for your info, when you send your computer back to the manufacturer, they're going to just restore it using the recovery CD, and laugh all day because of how idiotic you are.]]
9. Has your son radically changed his appearance?
Gibbons: "If your son has undergone a sudden change in his style of dress, you may have a hacker on your hands. Hackers tend to dress in bright, day-glo colors. They may wear baggy pants, bright colored shirts and spiky hair dyed in bright colors to match their clothes. They may take to carrying "glow-sticks" and some wear pacifiers around their necks. (I have no idea why they do this) There are many such hackers in schools today, and your son may have started to associate with them. If you notice that your son's group of friends includes people dressed like this, it is time to think about a severe curfew, to protect him from dangerous influences."

Me: In the section above Gibbons mentions that the creator of the linux kernel, Linyos Torovoltos is a computer hacker...to the left is a picture of him. Does he meet the description of a hacker acording to Gibbons? No because hes is NOT a hacker. [[I believer you're referring to the ever-growing group of stylists known as "ravers". They go to parties known as raves, and usually are on some form of sedative or the like. Special-K, i.e. Ketamine is highly popular, because it is easy to find and cheap to purchase. It is cat tranquilizer in small doses, and horse tranquilizer in large doses. Nextly, E, or extasy, is the next most popular drug. It is ingested in the form of a pill, and cause people to "roll" at raves, because of the intense lightshows. If your son was wearing raver clothing, more than likely you shouldn't worry about him being a hacker, but rather being under the influence of some drug or another. Nice detective work, Sherlock.]]
10. Is your son struggling academically?
Gibbons: "
If your son is failing courses in school, or performing poorly on sports teams, he may be involved in a hacking group, such as the infamous "Otaku" hacker association. Excessive time spent on the computer, communicating with his fellow hackers may cause temporary damage to the eyes and brain, from the electromagnetic radiation. This will cause his marks to slip dramatically, particularly in difficult subjects such as Math, and Chemistry. In extreme cases, over-exposure to computer radiation can cause schizophrenia, meningitis and other psychological diseases. Also, the reduction in exercise may cause him to lose muscle mass, and even to start gaining weight. For the sake of your child's mental and physical health, you must put a stop to his hacking, and limit his computer time drastically.
I encourage all parents to read through this guide carefully. Your child's future may depend upon it. Hacking is an illegal and dangerous activity, that may land your child in prison, and tear your family apart. It cannot be taken too seriously."
Me: Computers help chiI was googling around looking for something interesting and come across an article called "Is You Son a Computer Hacker?" by Reginald Gibbons. I thaught i would look interesting so i went and started reading... after a couple minuites i was very, very upset because the article was total BS!! After a little bit of thinking i thaught it might be a joke but i found that it was not...i was frustrated by his ignorance in writting about something he had apsolutly no clue about. I will give you an overview of the article with my thaughts on each part.
How to determine if your kid is a Hacker Acording to Reginald Gibbons
1. Has your son asked you to change ISPs?
Gibbons: "If your child is becoming a hacker, one of his first steps will be to request a change to a more hacker friendly provider."
Me: This is tottal BS...changing to a different ISP is not a sign of becoming a hacker...especialy if you are switching from slow AOL...
2. Are you finding programs on your computer that you don't remember installing?
Gibbons: "Your son will probably try to install some hacker software." ... "Popular hacker software includes 'Comet Cursor', 'Bonzi Buddy' and 'Flash'."
Me: . It is by no means a hacker program AT ALL. You would have to be a complete idiot to think so!! ...this is just a little app that is packed with spyware/malware/adware that helps you browse the internet...hackers have apsolutly no uses for this program...what are they going to do with it? ask the monkey what to do next? At the end of Gibbons list is 'Flash'...when i say this is was just shocked that somebody could be soo ignorant...Flash has no uses for hackers at all!! All it does is enhance the experiance of internet users.
3. Has your child asked for new hardware?
Gibbons: "Computer hackers are often limited by conventional computer hardware. They may request 'faster' video cards, and larger hard drives, or even more memory. " ... "If your son has requested a new 'processor' from a company called 'AMD', this is genuine cause for alarm. AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips. They use child labor extensively in their third world sweatshops, and they deliberately disable the security features that American processor makers, such as Intel, use to prevent hacking. AMD chips are never sold in stores, and you will most likely be told that you have to order them from internet sites. Do not buy this chip! This is one request that you must refuse your son, if you are to have any hope of raising him well."
Me: First off as a geek i love getting new hardware...not because i am a hacker and am "limited by conventional harware" but because i enjoy getting the best performance from my machine. Gibbons mentions that hackers may request hardware like a faster videocard, a larger harddrive or more memory...A hacker would not prosper by having a faster videocard..it would not effect him at all...most hacking is done through a console unlike most hacker movie show (eg. Swordfish and the hacking GUI). Then he comes to saying that "AMD is a third-world based company who make inferior, "knock-off" copies of American processor chips." This is the one of the stupidest thing i think i have ever heard... and just because they leave thier processors more open so they can be overclocked esiar does not mean they are more hacker friendly.
4. Does your child read hacking manuals?
Gibbons: "There are, unfortunately, many hacking manuals available in bookshops today. A few titles to be on the lookout for are: 'Snow Crash' and 'Cryptonomicon' by Neal Stephenson; 'Neuromancer' by William Gibson; 'Programming with Perl' by Timothy O'Reilly; 'Geeks' by Jon Katz; 'The Hacker Crackdown' by Bruce Sterling; 'Microserfs' by Douglas Coupland; 'Hackers' by Steven Levy; and 'The Cathedral and the Bazaar' by Eric S. Raymond." ... "If you find any of these hacking manuals in your child's possession, confiscate them immediately."
Me: Sure there are many hacker books on the market...it is an interesting topic.
5. How much time does your child spend using the computer each day?
Gibbons: "If your son spends more than thirty minutes each day on the computer, he may be using it to DOS other peoples sites." ... "This can take up to eight hours."
Me: Most teens don't spend thier time on the computer using Dos to gain control of other peoples computer...they spend their time playing games and don't harm anything. By the way Dos'ing is more commonly known as 'flooding'.
6. Does your son use Quake?
Gibbons: "Quake is an online virtual reality used by hackers. t is a popular meeting place and training ground, where they discuss hacking and train in the use of various firearms. Many hackers develop anti-social tendencies due to the use of this virtual world, and it may cause erratic behaviour at home and at school."
Me: Quake is a GAME not a virtual reality used by hackers to train. Train in the use of variouse firearms? It is just a game...a first person shooter...the guns are not real!!
7. Is your son becoming argumentative and surly in his social behaviour?
Gibbons: "As a child enters the electronic world of hacking, he may become disaffected with the real world. He may lose the ability to control his actions, or judge the rightness or wrongness of a course of behaviour. This will manifest itself soonest in the way he treats others. Those whom he disagrees with will be met with scorn, bitterness, and even foul language. He may utter threats of violence of a real or electronic nature."
Me: Just because a child is interested in computers doesn't mean he will become disconnected with the "real world". Hackers are people too, and they function like all other people...just becuase they are hackers doesn't mean they fit the hacker stereo type... Also note that adolence could be effecting thier behavior.
8. Is your son obsessed with "Lunix"?
Gibbons: "BSD, Lunix, Debian and Mandrake are all versions of an illegal hacker operation system, invented by a Soviet computer hacker named Linyos Torovoltos, before the Russians lost the Cold War. It is based on a program called 'xenix', which was written by Microsoft for the US government. These programs are used by hackers to break into other people's computer systems to steal credit card numbers. They may also be used to break into people's stereos to steal their music, using the "mp3" program. Torovoltos is a notorious hacker, responsible for writing many hacker programs, such as "telnet", which is used by hackers to connect to machines on the internet without using a telephone.
Your son may try to install 'lunix' on your hard drive. If he is careful, you may not notice its presence, however, lunix is a capricious beast, and if handled incorrectly, your son may damage your computer, and even break it completely by deleting Windows, at which point you will have to have your computer repaired by a professional."
Me: When i read this section i was enraged...Lunix is a usinx based operating system for the commador 64...if your kid is still using one of those you should consider upgrading. First off linux is not an illegal operating system!! Lunix is different from every other example Gibbons gave... the rest use the linux kernel where Lunix has it's own. The linux kernel developed by Linyos Torovoltos is not based on xenix but is inspired by Minix. I have no clue where Gibbons comes up with his facts but i have yet to find one that is true. I have no clue what gibbons was doing when he wrote this article but this section is TOTTAL BS and makes no sence what so ever.
9. Has your son radically changed his appearance?
Gibbons: "If your son has undergone a sudden change in his style of dress, you may have a hacker on your hands. Hackers tend to dress in bright, day-glo colors. They may wear baggy pants, bright colored shirts and spiky hair dyed in bright colors to match their clothes. They may take to carrying "glow-sticks" and some wear pacifiers around their necks. (I have no idea why they do this) There are many such hackers in schools today, and your son may have started to associate with them. If you notice that your son's group of friends includes people dressed like this, it is time to think about a severe curfew, to protect him from dangerous influences."
Me: In the section above Gibbons mentions that the creator of the linux kernel, Linyos Torovoltos is a computer hacker...to the left is a picture of him. Does he meet the description of a hacker acording to Gibbons? No because hes is NOT a hacker.
10. Is your son struggling academically?
Gibbons: "
If your son is failing courses in school, or performing poorly on sports teams, he may be involved in a hacking group, such as the infamous "Otaku" hacker association. Excessive time spent on the computer, communicating with his fellow hackers may cause temporary damage to the eyes and brain, from the electromagnetic radiation. This will cause his marks to slip dramatically, particularly in difficult subjects such as Math, and Chemistry. In extreme cases, over-exposure to computer radiation can cause schizophrenia, meningitis and other psychological diseases. Also, the reduction in exercise may cause him to lose muscle mass, and even to start gaining weight. For the sake of your child's mental and physical health, you must put a stop to his hacking, and limit his computer time drastically.
I encourage all parents to read through this guide carefully. Your child's future may depend upon it. Hacking is an illegal and dangerous activity, that may land your child in prison, and tear your family apart. It cannot be taken too seriously."
Me: Computers help childern learn...i am done commenting on Gibbons total disregard to the truth and the facts. [[Well since you bought a new computer, emissions standards have virtually eliminated all radiation by computers, disproving your brain and eye damage theory. Most hackers are very intelligent, and excel in such subjects as math and foreign languages. And for everyone's knowledge, meningitis is NOT A PSYCHOLOGICAL DISEASE!!! IT'S BACTERIAL!!!]]
Note: text enclosed by [[]] is quoted from here
Conclusion:
Answering Gibbons questions:
1. Yes...i have changed my ISP a couple times [i wanted a faster conection].
2. I have flash on my linux laptop (the other programs do not work on linux i believe)
3. Yes i have asked for new hardware for variose computers in my house.
4. Yes i read hacking manuals because they are interesting (The unofficial guide to ethical hacking)
5. I spend many many hours a day on my computer. A lot more than 30 minuites a day...if i had the restriction i would die.
6. I have never played Quake but i have played quake 4 and 3...
7. No...just because i am a geek doesn't mean i do not have a life
8. Yes i love linux :)
9. Sometimes for fun :)
10. I only struggle accademicly when i don't work
So...acording to Gibbons i am a hacker. (Note that Gibbons is using the term 'Hacker' in a foul way. As in breaking the law.) I am not denying that i am a hacker...i will leave it up to you to decide (see this [note the bottom text])
Note: the term hacker takes on many meanings. Some of which are:
1. One who is proficient at using or programming a computer; a computer buff.
2. One who uses programming skills to gain illegal access to a computer network or file
ldern learn...i am done commenting on Gibbons total disregard to the truth and the facts.
Note: text enclosed by [[]] is quoted from here
Conclusion:
Answering Gibbons questions:
1. Yes...i have changed my ISP a couple times [i wanted a faster conection].
2. I have flash on my linux laptop (the other programs do not work on linux i believe)
3. Yes i have asked for new hardware for variose computers in my house.
4. Yes i read hacking manuals because they are interesting (The unofficial guide to ethical hacking)
5. I spend many many hours a day on my computer. A lot more than 30 minuites a day...if i had the restriction i would die.
6. I have never played Quake but i have played quake 4 and 3...
7. No...just because i am a geek doesn't mean i do not have a life
8. Yes i love linux :)
9. Sometimes for fun :)
10. I only struggle accademicly when i don't work
So...acording to Gibbons i am a hacker. (Note that Gibbons is using the term 'Hacker' in a foul way. As in breaking the law.) I am not denying that i am a hacker...i will leave it up to you to decide (see this [note the bottom text])
Note: the term hacker takes on many meanings. Some of which are:
1. One who is proficient at using or programming a computer; a computer buff.
2. One who uses programming skills to gain illegal access to a computer network or file
Subscribe to:
Posts (Atom)










